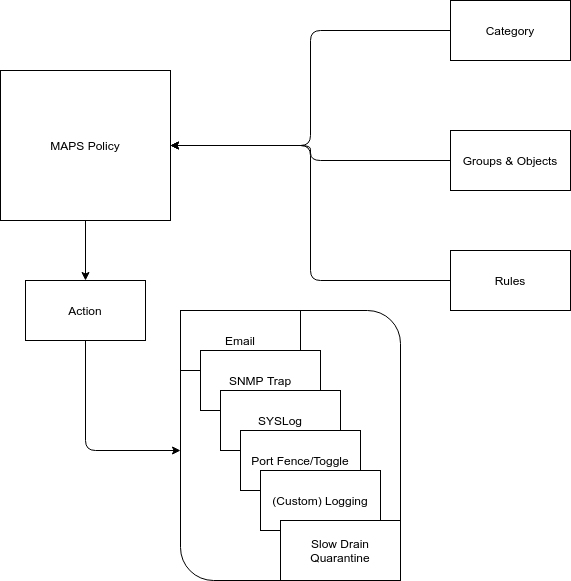
This topic is hardly ever touched when fabric designs are developed and discussed among storage engineers but for me this always sits on my TODO list before hooking up any HBA or array port. It is as important in the storage world as it has been in the IP networking sector for decades. Historically the reasoning to not pay attention to this topic was that the SAN was always deeply embedded in tightly controlled data-centres with strict access policies. Additionally the use of fibre-optics and relatively complex architectures to the storage un-inaugurated even more, unfairly, devalued the necessity of implementing security policies.

Let me make one thing clear: Being able to gain access to a storage infrastructures is like finding the holy grail for archaeologists. If no storage infrastructure security is implemented it will allow you to obtain ALL data for good or bad purposes but even worse it also allows the non-invited guest to corrupt and destroy it. With this chapter I will outline some of the procedures I consider a MUST and some which you REALLY should take a good look at and if possible implement them.
Continue reading →