Something none storage related. This article at “The Register” triggered me to write this post and explain why I don’t see this behaviour in my household. The trick is to configure DNS-over-HTTPS in your network.
For the non-technical people who read this the title may already be an incentive to not read any further but please bear with me.
Whenever you type something in your browsers address bar like erwinvanlonden.net” your computer has no idea what that means. The internet works with numbers as addresses and not names. As we as humans are extremely bad with numbers (what’s your mother-in-law’s phone number… now!!… too-late…:-) ) we tend to remember names much more easily. So that is why the internet folks back in the days designed some sort of “phone-book” where these domain names are translated to numbers and tell your browser to connect to that address.
DNS
That phonebook system is called DNS (Domain Name System) and is a distributed hierarchical list of domains from top level (.com, .net, .org) all the way down to names likes “www.what.does.this.button.do.com” (I made that up.). So when your computer does not know the number associated with that name it contacts a DNS server, and that is most often the server at your Internet Service Provider (ISP), and that server will then give your computer that number.
How ISP’s abuse that system
The above shows that basically every time you visit a website your ISP will know that and as such may create a user profile linked to your account. Depending on the country you live in and the privacy law’s that are effective in that country many ISP lean towards the boundaries of that law and have a fairly extensive view of your behaviour. Even though they may not have physically linked your connection to your name, address etc. , your profile will be technically linked to the connection you have with them.
The way they use that information is twofold.
1. They may serve you ads as part of a response of a webpage or
2 If a name you type in your browser does not exist their systems may direct you to a list of sponsored links that may be closely associated with the name you typed in.
Option two is the one that was described in the article at The Register. Both methods will generate revenue for that ISP at the expense of you. Further profiling may happen depending on the linked web-pages you then click on.
NXDOMAIN
So diving a bit in option 2. If a name you type in does not exist in the ISP’s DNS server what it first does is contact a DNS root server to see if there is another DNS server that may have that phone-book entry. If that is the case the query will be forwarded and at some stage returned to you. This all happens in the back ground. If that name however does not exist the DNS server answers with a NXDOMAIN response which basically means “Non Existing Domain”. That is the trigger where many ISP’s have configured their systems to hijack that response and redirect you to their sponsored links pages who then serve you a web-page based on your historical browsing profile.
This goes against all ethics and if you have such an ISP I would urge you look for another one who will clearly state that then don’t embark on such despicable behaviour.
Bypass the ISP
If you are limited in choice for whatever reason there may be a few other options.
- Configure your computer to use a different DNS server
- Use DNS-o-HTTPS end-to-end
- Use DNS-o-HTTPS via your edge-router
Option 1 is most often the easiest but does not guarantee that it will work. When you configure a different DNS server that request will obviously be sent to that address. Your ISP however may however “catch” that request and under the hood redirect that request to one of their DNS servers which in the end fully negates the purpose of you configuring a different DNS server as the behaviour will be the same.
Option 2 is therefore the quickest and easiest of the three. Most browsers these days allow you to send DNS requests to a variety of DNS providers over HTTPS. That means these request will be encrypted in the same way as all other https web-pages and as such your ISP is not able to differentiate the content of your request nor can it see what the response is. They therefore are unable to hijack that response and redirect you to one of their pages.
DNS over HTTP proxy
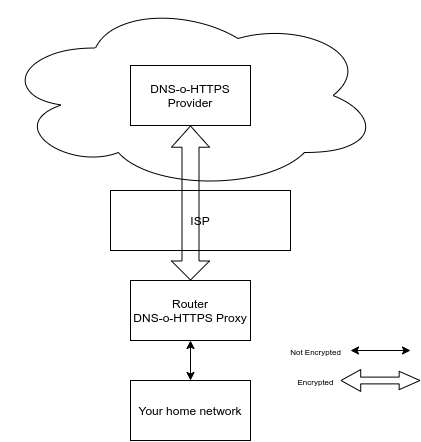
The above may work fine if you’re the only one in your household but if your partner, kids, guests etc also use your connection to the web it’ll do no good to them as you need to configure each individual browser like that. You also don’t have much control over the behaviour of that browser when updates are done or when someone clicks the “reset-to-default” button. That is where a DNS-over-HTTPS proxy comes in handy. This requires a fair bit of knowledge and also depends on your home routers’ capability to do that. Many modern routers do provide this functionality out of the box. If you’re somewhat of a geek you may even have tried open-source software like DD-wrt or OpenWRT. I use the last one personally and I have configured that option 3.
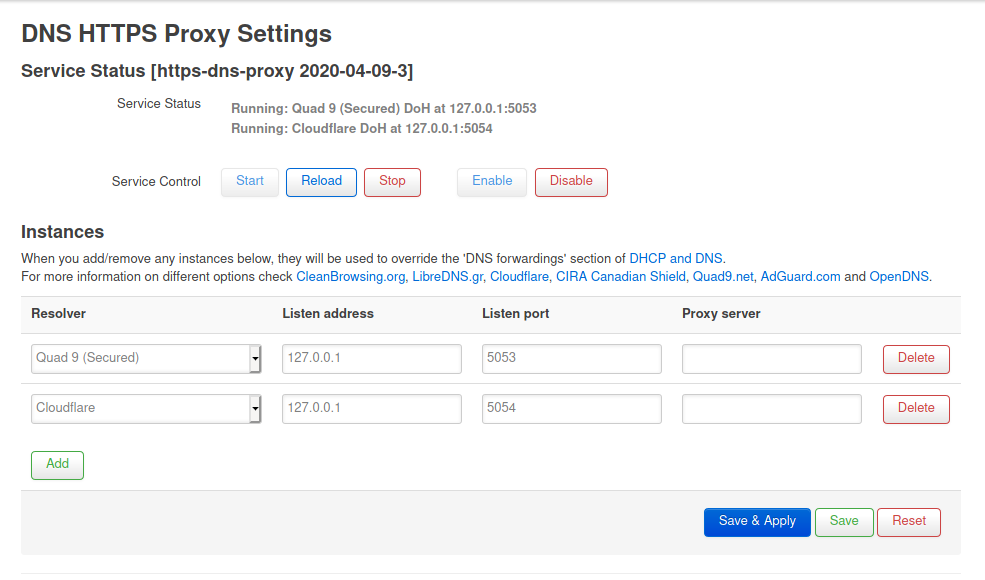
In OpenWRT you have to install the DNS-o-HTTPS Proxy package as well as the Luci gui extension. Configure the DNS providers to your liking (Also check their policies with regards to logging etc….) An example below.
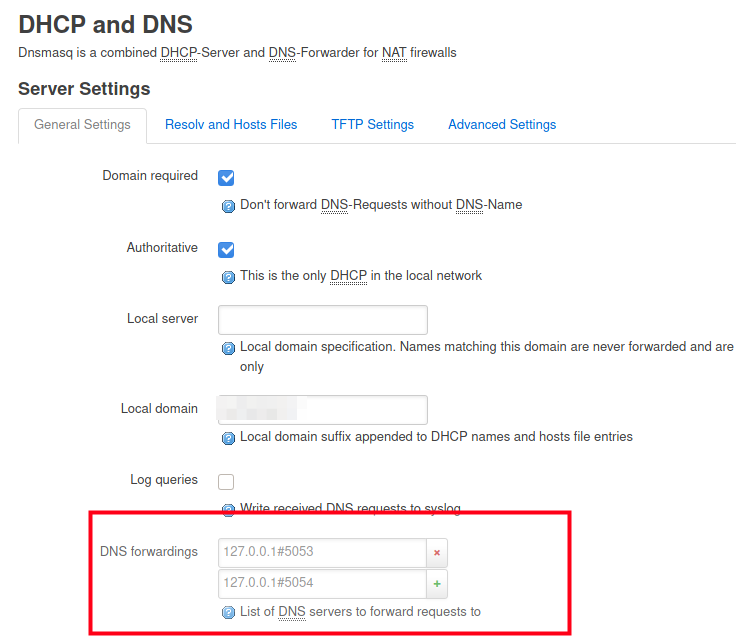
In your DNS settings of your router you then have to set that all DNS requests from your clients should go to one of the addresses you configured in the DNS proxy settings.
This ensure that all the DNS requests of all the computers connected to the router will be tunnelled through that DNS-o-HTTPS proxy and thus these requests will then be forwarded in encrypted format to that DNS provider via your ISP. That ISP cannot trace the content nor the response as mentioned before.
The above setup still does not prevent one of your connected computers to have their own setting and configure a different DNS server other than your router. This would still traverse that request to go un-encrypted to that DNS provider via your ISP. That request may still be intercepted as previously shown. In order to circumvent that we may configure our firewall rule to basically do the same as your ISP’s. We intercept all DNS requests and send this to the DNS process on your router.
As simple way to do this is similar like below where we add a rule telling the router to redirect all DNS requests to the local router:
iptables -t nat -N DNS
iptables -N DNS
iptables -t nat -A DNS -s 192.168.1.0/24 -p udp –dport 53 -j DNAT –to 192.168.1.1:53
iptables -t nat -I PREROUTING -p udp –dport 53 -j DNS
iptables -I INPUT -p udp –dport 53 -j DNS
Some technicalities: The fire two lines create a new iptables chain, The third creates the redirect rule in the DNS chain to have all DNS request (These are sent on udp port 53) from subnet 192.168.1.0/24 sent to the DNS resolver process on the router (192.168.1.1) also listening on port 53.
The 4th and 5th line tell the firewall to have all DNS requests sent to the DNS chain where they will be caught by the rule.
So even if a computer on your network is directing DNS requests to a different server your router will in the background ensure that this is then securely forwarded to the DNS provider you configured in the DNS-proxy settings.
Just so you know, the above is just a very small snippet of what is possible. My DNS resolver and firewall configuration is far more extensive with different time settings, domain exclusions, logging facilities etc. etc. You have to keep your kids safe in any possible way you can, keep the creeps out and hopefully prevent them from being exposed to the nasty side of the web.
Hope this helps somewhat.
Regards,
Erwin