The first thing to think of when creating a Brocade storage network has nothing to do with a switch configuration at all. Its about the surrounding management landscape. There are numerous management software options available from a multitude of vendors including Brocade with Network Advisor. If you have purchased BNA then congratulations, you have a solid toolkit in your hands to take care of nearly everything you need to manage, maintain and troubleshoot the SAN. Despite this there are more things to take into account.
A good sysadmin will also make sure a fallback scenario is operational and in equal, if not better, shape then his primary administration tool. In this section I’ll describe the toolkit I used over the years to maintain a storage environment.
The management network
One of the thing we rely on most heavily is proper access to the switch management ports. Un-obstructed access without needing to go through firewalls, network switch ACL’s and other obstacles that could interfere with traffic to these management ports is preferred. The best method of achieving this is to have a separate management network which is physically disconnected from any other production network and only has access to equipment for management purposes. Separate VPN access to that network is useful for remote access. If that is not possible an isolated vlan with the same un-obstructed characteristics is a good alternative.
Well known management ports like ssh, http(s), (s)ftp, snmp, SMI etc should all be opened up. This may seem like a security vulnerability but fencing this off from the out-side world isn’t that difficult. Putting access restrictions on management interfaces will lead to disastrous events in the future. One example is of being locked out of an https session and you have no way of accessing that FC-switch in any other way. Its pretty annoying if this switch sits in a dark site some 500 kilometres away and has locked up a zone-change which prevents you from doing any provisioning at all. CLI access would be the only method to recover in this instance however if ssh is blocked in a network ACL and telnet is disabled on the FC-switch you have a long driver ahead of you to resolved the problem or start begging to the security people to open up some ports on the IP network.
Serial port access
One of the things I ALWAYS had in place was serial port (RS323) access to everything that had this access method. If it meant I had to ramp up a PC with some serial ports or buy equipment like the DECServer 90 (see my heritage. :-)) which gives you direct access to serial interfaces via the network. It acts like a IP to RS323 gateway. An alternative is a Vlinx ESR converter which allows you to do the same thing.
The reason why you would need access to the serial port is that even if the network-stack on the management port is inoperable or if you made a mistake in configuring IP addresses, subnet mask or default gateway settings, you are still able to access that switch and correct the problem from anywhere in the world. Sometimes when software bug has hit a switch and the switch hangs on a boot-prompt waiting for input the serial port is the only way of getting to the switch’ interface. Since the NeoScale e500 PPC doesn’t work with a BIOS interface the only method of adjusting the boot behaviour of the switch is via environment variables. This is also achieved only by accessing the serial interface. Especially during firmware upgrades when something goes wrong, RS323 access is invaluable. Make sure you have this sorted.
Tools
Given the fact my primary work environment consists of Linux systems I have no shortage of tools, scripting and programming environments and server based applications that allow me to do just about everything I need. A simple “yum install xyz” or “apt-get install xyz” creates the application environment I need. On a windows system this might be somewhat more cumbersome. Not only doesn’t Windows provide the majority of tools right out of the box some really handy tools even need to be purchased plus the installation and updates of these tools are not as straightforward as on Linux. Nevertheless I’ll focus on the Windows side for now and the Linux admins are most of the times quick enough to find their platform alternative.
Below a list of tools I use (or have used) in addition (or in absence of) Brocade Network Advisor or one of its predecessors.
- FileZilla FTP Server by Tim Kosse. Easy to use FTP server, free of charge.
- Putty You know the one.
- Cygwin to create a near GNU compatible toolkit environment on Windows.
- The majority of the free SolarWinds toolkit
- Wireshark – must have for any sysadmin
- Storageim – Storage SMI Browser. Very useful to gain access to switches (or storage equipment in general via the SMI API interfaces.
- JDSU Xgig (formerly Finisar) FC trace analyser and jammer (not free but a must have for support personnel !)
(Remember that if you like a tool or use it often consider a donation to the project.)
From the above there is one I would like to touch on since that is the one I’m discussing in subsequent chapters and that is the FileZilla FTP server. The FTP server can be configured (and sometimes is by default) to prevent DOS attacks. Basically it prevents a maximum number of concurrent connections from one or more IP addresses or users.
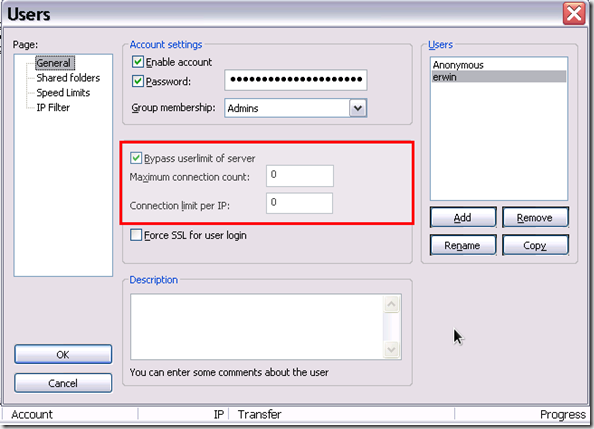
Best practise is to create a single user with a very long password. (64 characters would be great. You don’t have to remember it by heart and we’ll use this username and password later on. Simply do a “date | sha256sum” and it’ll be close enough to cover all security purposes. According to https://howsecureismypassword.net/ it would take and astronomical amount of time to hack this anyway.) Bypass the server restrictions and set both values to 0. Do NOT tick the “Force SSL” since the FTP client process in FOS does not use ssl.
In the next chapter I’ll discuss the reference architecture and the relation to the some other settings in the ftp-server.